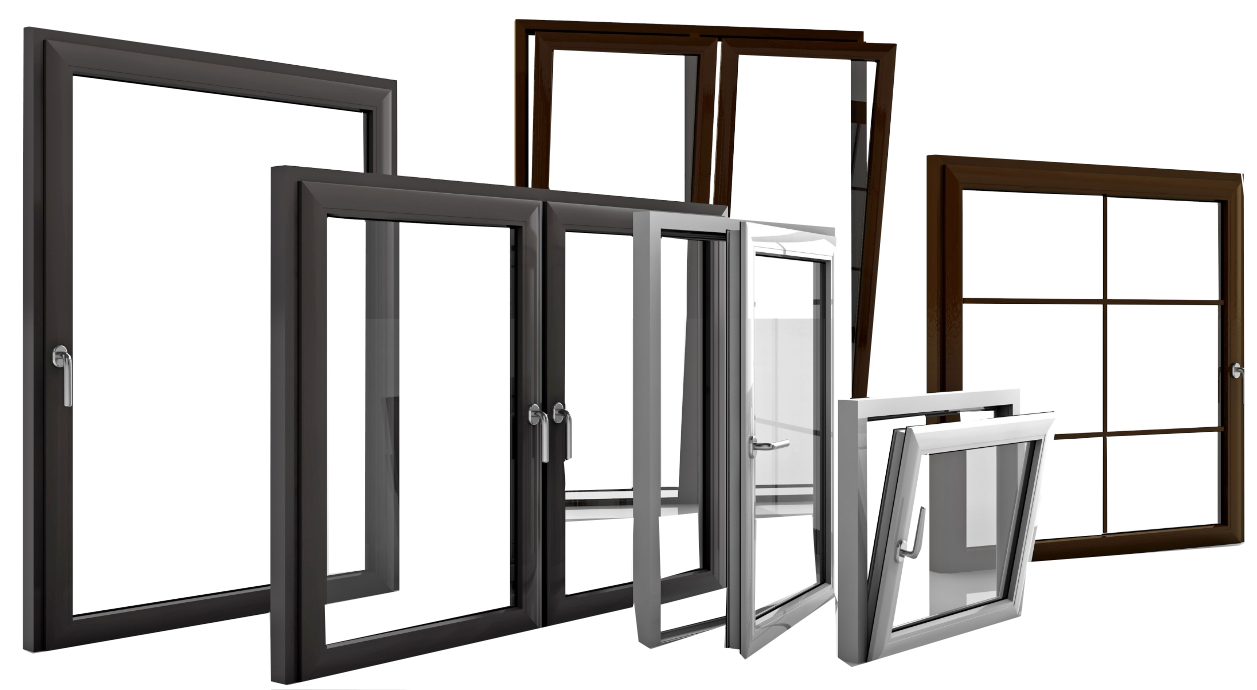
Top-Plast Lubań-producent okien drzwi pcv veka,aluplast oraz aluminum ponzio

Usługi montażu i nasze produkty oferujemy między innymi w następujących lokalizacjach...
-
Okna Lubań/ Okna pcv Lubań/ Okna aluminium Lubań/ Drzwi pcv Lubań/ Drzwi aluminium Lubań/ Drzwi przesuwne HST Lubań
-
Okna Zgorzelec/ Okna aluminium Zgorzelec/ Drzwi pcv Zgorzelec/ Drzwi aluminium Zgorzelec/ Drzwi przesuwne HST Zgorzelec
-
Okna Bogatynia/Okna pcv Bogatynia/ Okna aluminium Bogatynia/ Drzwi pcv Bogatynia/ Drzwi aluminium Bogatynia/ Drzwi przesuwne HST Bogatynia
-
Okna Jelenia Góra/Okna pcv Jelenia Góra/ Okna aluminium Jelenia Góra/ Drzwi pcv Jelenia Góra/ Drzwi aluminium Jelenia Góra/ Drzwi przesuwne HST Jelenia Góra
-
Okna Bolesławiec/Okna pcv Bolesławiec/ Okna aluminium Bolesławiec/ Drzwi pcv Bolesławiec/ Drzwi aluminium Bolesławiec/ Drzwi przesuwne HST Bolesławiec
-
Okna Legnica/Okna pcv Legnica/ Okna aluminium Legnica/ Drzwi pcv Legnica/ Drzwi aluminium Legnica/ Drzwi przesuwne HST Legnica
-
Okna Wrocław/Okna pcv Wrocław/ Okna aluminium Wrocław/ Drzwi pcv Wrocław/ Drzwi aluminium Wrocław/ Drzwi przesuwne HST Wrocław
-
Okna Złotoryja/Okna pcv Złotoryja/ Okna aluminium Złotoryja/ Drzwi pcv Złotoryja/ Drzwi aluminium Złotoryja/ Drzwi przesuwne HST Złotoryja
-
Okna Bogatynia/Okna pcv Bogatynia/ Okna aluminium Bogatynia/ Drzwi pcv Bogatynia/ Drzwi aluminium Bogatynia/ Drzwi przesuwne HST Bogatynia
-
Okna Świeradów/Okna pcv Świeradów/ Okna aluminium Świeradów/ Drzwi pcv Świeradów/ Drzwi aluminium Świeradów/ Drzwi przesuwne HST Świeradów
-
Okna Karpacz/Okna pcv Karpacz/ Okna aluminium Karpacz/ Drzwi pcv Karpacz/ Drzwi aluminium Karpacz/ Drzwi przesuwne HST Karpacz
-
Okna Podgórzyn/Okna pcv Podgórzyn/ Okna aluminium Podgórzyn/ Drzwi pcv Podgórzyn/ Drzwi aluminium Podgórzyn/ Drzwi przesuwne HST Podgórzyn
-
Okna Jelenia Góra/Okna pcv Jelenia Góra/ Okna aluminium Jelenia Góra/ Drzwi pcv Jelenia Góra/ Drzwi aluminium Jelenia Góra/ Drzwi przesuwne HST Jelenia Góra
-
Okna Gryfów Śląski/Okna pcv Gryfów Śląski/ Okna aluminium Gryfów Śląski/ Drzwi pcv Gryfów Śląski/ Drzwi aluminium Gryfów Śląski/ Drzwi przesuwne HST Gryfów Śląski
-
Okna Lwówek Śląski/Okna pcv Lwówek Śląski/ Okna aluminium Lwówek Śląski/ Drzwi Lwówek Śląski / Drzwi aluminium Lwówek Śląski/ Drzwi przesuwne HST Lwówek Śląski
-
Okna Mirsk/Okna pcv Mirsk/ Okna aluminium Mirsk/ Drzwi pcv Mirsk/ Drzwi aluminium Mirsk/ Drzwi przesuwne HST Mirsk //Mirsk
-
Okna Szklarska Poręmba/Okna pcv Szklarska Poręmba/ Okna aluminium Szklarska Poręmba/ Drzwi pcv Szklarska Poręmba/ Drzwi aluminium Szklarska Poręmba/ Drzwi przesuwne HST Szklarska Poręmba
-
Okna Środa Śląska/Okna pcv Środa Śląska/ Okna aluminium Środa Śląska/ Drzwi pcv Środa Śląska/ Drzwi aluminium Środa Śląska/ Drzwi przesuwne HST Środa Śląska
-
Okna Szprotawa/Okna pcv Szprotawa/ Okna Szprotawa/Drzwi pcv Szprotawa/ Drzwi aluminium Szprotawa/ Drzwi przesuwne HST Szprotawa
-
Okna Lubin/Okna pcv Lubin/ Okna aluminium Lubin/ Drzwi pcv Lubin/ Drzwi aluminium Lubin/ Drzwi przesuwne HST Lubin
-
Okna Chojnów/Okna pcv Chojnów/ Okna aluminium Chojnów/ Drzwi pcv Chojnów/ Drzwi aluminium Chojnów/ Drzwi przesuwne HST Chojnów
-
Okna Iłowa/Okna pcv Iłowa/ Okna aluminium Iłowa/ Drzwi pcv Iłowa/ Drzwi aluminium Iłowa/ Drzwi przesuwne HST Iłowa
-
Okna Świętoszów/Okna pcv Świętoszów/ Okna aluminium Świętoszów/ Drzwi pcv Świętoszów/ Drzwi aluminium Świętoszów/ Drzwi przesuwne HST Świętoszów
-
Okna Żagań/Okna pcv Żagań/ Okna aluminium Żagań/ Drzwi pcv Żagań/ Drzwi aluminium Żagań/ Drzwi przesuwne HST Żagań
-
Okna Żary/Okna pcv Żary/ Okna aluminium Żary/ Drzwi pcv Żary/ Drzwi aluminium Żary/ Drzwi przesuwne HST Żary
-
Okna Zielona Góra/Okna pcv Zielona Góra/ Okna aluminium Zielona Góra/ Drzwi pcv Zielona Góra/ Drzwi aluminium Zielona Góra/ Drzwi przesuwne HST Zielona Góra
-
Okna Wołów/Okna pcv Wołów/ Okna aluminium Wołów/ Drzwi pcv Wołów/ Drzwi aluminium Wołów/ Drzwi przesuwne HST Wołów
-
Okna Brzeg Dolny/Okna pcv Brzeg Dolny/ Okna aluminium Brzeg Dolny/ Drzwi pcv Brzeg Dolny/ Drzwi aluminium Brzeg Dolny/ Drzwi przesuwne HST Brzeg Dolny
-
Okna Brzeg Dolny/Okna pcv Brzeg Dolny/ Okna aluminium Brzeg Dolny/ Drzwi pcv Brzeg Dolny/ Drzwi aluminium Brzeg Dolny/ Drzwi przesuwne HST Brzeg Dolny
-
Okna Kamienna Góra/Okna pcv Kamienna Góra/ Okna aluminium Kamienna Góra/ Drzwi pcv Kamienna Góra/ Drzwi aluminium Kamienna Góra/ Drzwi przesuwne HST Kamienna Góra
-
Okna Wałbrzych/Okna pcv Wałbrzych/ Okna aluminium Wałbrzych/ Drzwi pcv Wałbrzych/ Drzwi aluminium Wałbrzych/ Drzwi przesuwne HST Wałbrzych
Firma Top-Plast Lubań (dolnośląskie) to doświadczony producent okien i drzwi z PCV oraz aluminium. Od ponad 27 lat działamy zarówno na lokalnym rynku (Lubań, Zgorzelec, Bogatynia, Jelenia Góra, Bolesławiec, Legnica, Wrocław), jak i międzynarodowym. Współpracujemy z renomowanymi liderami branży stolarki, takimi jak Veka, Aluplast, Ponzio, Winkhaus i Press-Glass. Nasza bogata oferta obejmuje również bramy garażowe, parapety, rolety, żaluzje fasadowe i wiele innych. Zapraszamy do zapoznania się z naszą kompleksową ofertą okien PCV i okna aluminium marki Veka i Aluplast, dostosowaną do Państwa indywidualnych potrzeb. Obsługujemy również tereny Szklarskiej Poręby, Karpacza, Świeradowa-Zdroju i Pieńska W razie jakichkolwiek pytań zapraszamy do kontaktu z naszym zespołem.
Okna i drzwi PCV i aluminium – Twój sprawdzony Producent w Bolesławcu, Legnicy, Jeleniej Górze, Złotoryi, Bogatyni, Zgorzelcu, Świeradowie, Karpaczu oraz Wrocławiu
Czy szukasz profesjonalnego producenta wysokiej jakości okien i drzwi PCV oraz aluminium w regionie Bolesławiec, Legnica, Jelenia Góra, Złotoryja, Bogatynia, Zgorzelec, Świeradów, Karpacz i Wrocław? Nasza firma to Twoje rozwiązanie! Specjalizujemy się w produkcji, sprzedaży oraz montażu szerokiego wyboru stolarki budowlanej, w tym okien, drzwi, rolet, parapetów i bram garażowych.
Jako czołowy producent okien pcv ,drzwi PCV oraz aluminium i okien aluminium w regionie, możemy zagwarantować najwyższą jakość naszych produktów. Korzystamy z renomowanych systemów Veka, Ponzio i Aluplast, co pozwala nam spełnić nawet najbardziej wymagające oczekiwania naszych klientów. Oferujemy szeroki wybór modeli, w tym Veka Sofiline 82 MD, Veka Perfectline, Aluplast Ideal 4000, Aluplast Ideal 7000, Veka Motion, Ponzio 78 NHI oraz Ponzio PE96, które zapewniają nie tylko doskonałą izolację termiczną i akustyczną, ale także trwałość i estetyczny wygląd.
Nie tylko dostarczamy wysokiej jakości produkty, ale również zapewniamy kompleksową obsługę. Nasz doświadczony zespół zajmie się nie tylko produkcją i sprzedażą, ale także profesjonalnym montażem stolarki oraz transportem. Dzięki temu możemy zapewnić naszym klientom pełną satysfakcję i gwarantować, że ich zamówienie zostanie zrealizowane w terminie i z najwyższą starannością.
W naszej ofercie znajdują się również rolety, parapety i bramy garażowe, które doskonale uzupełnią Twoją stolarkę budowlaną. Możesz być pewny, że wszystkie dodatki do naszych okien i drzwi są wykonane zgodnie z najwyższymi standardami jakości, zapewniając nie tylko funkcjonalność, ale także estetyczny wygląd Twojego domu.
Jeśli szukasz sprawdzonego producenta okien pcv, drzwi PCV oraz alu oraz okien aluminium w regionie Bolesławiec, Legnica, Jelenia Góra, Złotoryja, Bogatynia, Zgorzelec, Świeradów, Karpacz i Wrocław, to jesteśmy tutaj, aby Ci pomóc! Skontaktuj się z nami już dziś, aby dowiedzieć się więcej o naszych produktach i usługach. Gwarantujemy najwyższą jakość, profesjonalizm i pełne zadowolenie naszych klientów.
Czy szukasz profesjonalnego producenta wysokiej jakości okien i drzwi PCV oraz aluminium w regionie Bolesławiec, Legnica, Jelenia Góra, Złotoryja, Bogatynia, Zgorzelec, Świeradów, Karpacz i Wrocław? Nasza firma to Twoje rozwiązanie! Specjalizujemy się w produkcji, sprzedaży oraz montażu szerokiego wyboru stolarki budowlanej, w tym okien, drzwi, rolet, parapetów i bram garażowych.
Jako czołowy producent okien pcv ,drzwi PCV oraz aluminium i okien aluminium w regionie, możemy zagwarantować najwyższą jakość naszych produktów. Korzystamy z renomowanych systemów Veka, Ponzio i Aluplast, co pozwala nam spełnić nawet najbardziej wymagające oczekiwania naszych klientów. Oferujemy szeroki wybór modeli, w tym Veka Sofiline 82 MD, Veka Perfectline, Aluplast Ideal 4000, Aluplast Ideal 7000, Veka Motion, Ponzio 78 NHI oraz Ponzio PE96, które zapewniają nie tylko doskonałą izolację termiczną i akustyczną, ale także trwałość i estetyczny wygląd.
Nie tylko dostarczamy wysokiej jakości produkty, ale również zapewniamy kompleksową obsługę. Nasz doświadczony zespół zajmie się nie tylko produkcją i sprzedażą, ale także profesjonalnym montażem stolarki oraz transportem. Dzięki temu możemy zapewnić naszym klientom pełną satysfakcję i gwarantować, że ich zamówienie zostanie zrealizowane w terminie i z najwyższą starannością.
W naszej ofercie znajdują się również rolety, parapety i bramy garażowe, które doskonale uzupełnią Twoją stolarkę budowlaną. Możesz być pewny, że wszystkie dodatki do naszych okien i drzwi są wykonane zgodnie z najwyższymi standardami jakości, zapewniając nie tylko funkcjonalność, ale także estetyczny wygląd Twojego domu.
Jeśli szukasz sprawdzonego producenta okien pcv, drzwi PCV oraz alu oraz okien aluminium w regionie Bolesławiec, Legnica, Jelenia Góra, Złotoryja, Bogatynia, Zgorzelec, Świeradów, Karpacz i Wrocław, to jesteśmy tutaj, aby Ci pomóc! Skontaktuj się z nami już dziś, aby dowiedzieć się więcej o naszych produktach i usługach. Gwarantujemy najwyższą jakość, profesjonalizm i pełne zadowolenie naszych klientów.
Poszukujemy osób do pracy w dziale handlowym. Więcej informacji poniżej:
Szukają Państwo możliwości dotacji w zakresie stolarki okiennej i drzwiowej? Zapraszamy do zapoznania się z niniejszymi informacjami.

PRODUKTY

JAKOŚĆ POPARTA DOŚWIADCZENIEM!!!
PRODUCENT OKIEN DRZWI PCV I ALUMINUM OD 27 LAT!!!
Co sądzą o naszych produktach nasi klienci?
JAK KLIENCI OCENIAJĄ NASZE PRODUKTY??-OKNA PCV,DRZWI I INNE